Comprehensive Guide to IP (IPv4 / IPv6) – Key Points, Practices, and Pitfalls Engineers Should Master
Comprehensive Guide to IP (IPv4 / IPv6) – Key Points, Practices, and Pitfalls Engineers Should Master
IP addresses may look simple (just a string of numbers), but network design, troubleshooting, and security optimization all hinge on a deep understanding of IP. This article uses the quick‑reference points from the accompanying image as a skeleton, adding detail and practical knowledge to provide both hands‑on guidance and theoretical depth, enabling engineers to quickly get up to speed when designing subnets, debugging connectivity, migrating, or writing documentation.
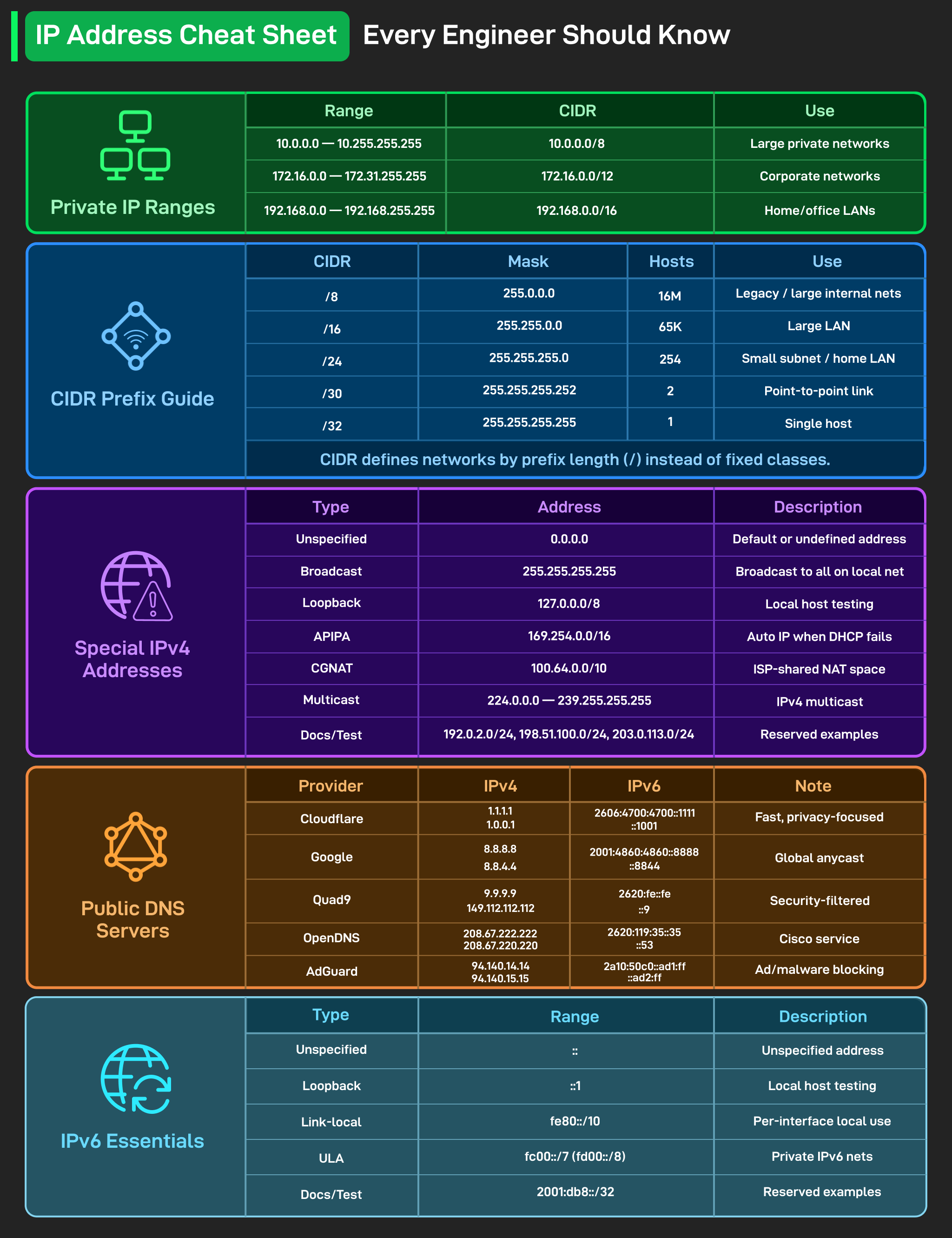
1. IPv4 Private Address Space and Usage (RFC 1918)
Common private ranges (not routable on the public Internet):
10.0.0.0/8– Large private networks (enterprise / data center).172.16.0.0/12– Medium‑sized enterprise networks (172.16.0.0 – 172.31.255.255).192.168.0.0/16– Home / office LANs (most consumer routers default to this range).
Purpose of private addresses: internal LAN communication + Internet access via NAT (or CGNAT). When designing, avoid address collisions with partners or vendors (plan addresses for inter‑connects or use NAT).
2. CIDR and Subnet Size (Prefix, Mask, and Usable Host Count)
CIDR (Classless Inter‑Domain Routing) uses a /n prefix to denote network length. Common examples (as shown in the image):
Usable host count calculation (traditional case):
Usable hosts =2^(32 - prefix) - 2(subtract network and broadcast addresses). Note:/31and/32have special cases (see below).
Below we calculate each prefix listed in the image (step‑by‑step to avoid mistakes):
/8:- 32 − 8 = 24
- 2^24 = 16,777,216
- 16,777,216 − 2 = 16,777,214 (≈16 M usable hosts)
/16:- 32 − 16 = 16
- 2^16 = 65,536
- 65,536 − 2 = 65,534 (≈65 K)
/24:- 32 − 24 = 8
- 2^8 = 256
- 256 − 2 = 254 (common small LAN / home network)
/30:- 32 − 30 = 2
- 2^2 = 4
- 4 − 2 = 2 (used for point‑to‑point links)
/32:- 32 − 32 = 0
- 2^0 = 1
/32represents a single host address (single‑host routing entry)
Special rules:
- RFC 3021 allows
/31to be used for point‑to‑point links (both addresses usable), avoiding the “waste” of two addresses. /32is a single address (common in router static routes, host table entries, bindings, etc.).- For modern network tools, when calculating “usable hosts” always consider whether your devices/protocols need to reserve broadcast or network addresses explicitly.
Subnetting example: split a /24 into /26 (increase prefix from 24 to 26, adding 2 bits for network):
/26usable addresses: 32 − 26 = 6; 2^6 = 64; 64 − 2 = 62 (each /26 has 62 usable hosts).
3. IPv4 Special Addresses and Reserved Ranges
Understanding these addresses is critical for troubleshooting and design:
0.0.0.0(Unspecified) – Default/undefined address (used at boot or for routing).- Broadcast
255.255.255.255– Local link broadcast (restricted to the local network). - Loopback
127.0.0.0/8(commonly127.0.0.1) – Host testing. - APIPA
169.254.0.0/16– Self‑assigned when DHCP fails (link‑local). - CGNAT
100.64.0.0/10– ISP‑internal shared NAT (reserved to address IPv4 exhaustion). - Multicast
224.0.0.0–239.255.255.255– IPv4 multicast addresses (used by mDNS, RTP, etc.). - Documentation/test:
192.0.2.0/24,198.51.100.0/24,203.0.113.0/24– for documentation examples, should not be routed on the public Internet.
4. Public DNS Resolvers (Quick Reference and Practical Advice)
The image lists common public DNS resolvers (IPv4 / IPv6) and their characteristics, useful for comparison in engineering practice:
- Cloudflare:
1.1.1.1/1.0.0.1(IPv62606:4700:4700::1111), privacy‑focused and fast; supports DoH/DoT. - Google:
8.8.8.8/8.8.4.4(IPv62001:4860:4860::8888), global anycast, stable. - Quad9:
9.9.9.9/149.112.112.112(IPv62620:fe::fe), emphasizes security filtering (blocks malicious domains). - OpenDNS (Cisco):
208.67.222.222/208.67.220.220, enterprise version offers policy control. - AdGuard DNS:
94.140.14.14/94.140.15.15, can block ads/malicious domains.
Practical points:
- Anycast public resolvers reduce latency and improve availability.
- Consider privacy (DoH/DoT) and compliance (some resolvers log queries); choose a resolver that fits organizational policy.
- In multi‑site architectures, a unified DNS strategy (caching, upstream resolvers, ACLs) aids troubleshooting and acceleration.
5. IPv6 Basics and Differences (Quick Reference)
Key IPv6 types and notes:
- Unspecified
::(unspecified). - Loopback
::1. - Link‑local
fe80::/10(each interface has one, used for neighbor discovery, auto‑configuration). - ULA (Unique Local Address)
fc00::/7(commonlyfd00::/8) – similar to IPv4 private addresses. - Documentation
2001:db8::/32– for documentation examples, should not be routed on the public Internet.
Main differences between IPv6 and IPv4:
- Huge address space (128‑bit), alleviates exhaustion.
- No broadcast (multicast replaces it).
- Enhanced neighbor discovery (ND) and auto‑configuration (SLAAC) – typically use ICMPv6.
- End‑to‑end addressing is preferred (usually no NAT); however NAT64, NAT66, etc., still exist for transition.
- IPv6 network design focuses on subnet planning (commonly /64 subnets for host auto‑configuration).
6. Practical Impact of NAT and CGNAT
NAT remains a core technology of the IPv4 era: it maps private addresses to public ones, solving address scarcity but introducing side effects:
- Pros: saves public addresses, provides basic host isolation.
- Cons: breaks end‑to‑end connectivity, hampers point‑to‑point protocols (SIP, FTP with embedded addresses), complicates inbound connections (port mapping/UPnP/ALG), increases complexity and log correlation difficulty.
- CGNAT (Carrier‑Grade NAT): ISPs share a public IP across many customers, causing a single public IP to map to multiple endpoints, affecting IP‑based access control, blacklisting, and traffic metering.
Design advice: expose necessary services via port mapping or reverse proxy within the LAN; in the long term, push IPv6 deployment to reduce reliance on NAT.
7. Common Commands & Troubleshooting Tips
- View local address (Linux):
ip addr show; (Windows):ipconfig /all. - View routing table (Linux):
ip route show; (Windows):route print. - Test connectivity:
ping,traceroute/tracert. - Subnet calculation tools:
ipcalc,sipcalc,subnetcalc. - DNS test:
dig +short example.com @1.1.1.1,nslookup. - Layer‑2 capture:
tcpdump(Linux) orWireshark(cross‑platform) to observe ARP/ND, DHCP flows, and anomalous packets.
Troubleshooting flow example:
- If no connectivity, first check the link layer (link lights, switch port, ARP/ND).
- If link is fine, verify IP configuration (DHCP lease, default gateway, DNS).
- Perform
pingfrom host → gateway → upstream DNS → external IP (e.g., 8.8.8.8) → domain (e.g., google.com). Pinpoint the failure step.
8. IPv6 Deployment, Transition, and Migration Strategies
In practice, IPv4 and IPv6 coexist. Common transition strategies:
- Dual Stack: ideal; hosts run both IPv4 and IPv6 simultaneously.
- Tunneling: 6in4, 6rd, Teredo (for environments where IPv6 is not directly routable).
- Translation: NAT64 + DNS64 for IPv6‑only clients to reach IPv4‑only services.
- Proxy / Application‑level gateway: protocol adaptation at the application layer (e.g., reverse proxy).
During migration, focus on:
- Auditing IP‑dependent systems (ACLs, monitoring, WAF, log analysis).
- Ensuring security devices (firewalls, IDS/IPS) support IPv6 / ICMPv6 policies (incorrect ICMPv6 handling can block ND and break the network).
- Publishing both A (IPv4) and AAAA (IPv6) records for services.
9. Security and Operations Recommendations
- Ingress / Egress filtering (BCP 38): block IP spoofing and amplification attacks.
- Least‑privilege principle: fine‑grained subnetting, ACLs, VLANs, security groups to isolate trust domains.
- Monitoring & logging: collect gateway, NAT, DNS logs for forensics and attack detection.
- DNS security: use DNS over TLS/HTTPS (DoT/DoH) and DNSSEC (signature verification) to enhance privacy and integrity.
- Upgrade strategy: regularly review private address planning to avoid cross‑vendor conflicts; protect ICMPv6/ND with RA Guard, ND inspection.
10. Engineering Practices and Best‑Practice Checklist
- Subnet planning: start with an address plan (purpose, site, redundancy, future growth) to avoid ad‑hoc allocation.
- External services: prefer reverse proxies or load balancers for unified exit and policy management (certificates, WAF, access control).
- IPv6: enable dual stack in test environments first, then gradually add AAAA records to critical services and monitor SLA.
- DNS: choose resolvers based on speed, privacy, filtering; provide different strategies for internal vs. external resolution.
- Automation: use IaC (Terraform, Ansible) to manage network configuration, preventing manual errors and drift.
- Test cases: include regression tests for NAT, CGNAT, IPv6‑only clients accessing IPv4 services.
Conclusion – From “Numbers” to “Relationships”
IP is more than a “number that lets you connect”; it embodies network boundaries, security models, interconnectivity, and evolution paths. Grasping CIDR bit‑math, mastering special address semantics, understanding the real‑world impact of NAT/CGNAT, and preparing for IPv6 are essential for every network, backend, or operations engineer. This article expands the quick‑reference points from the image into a deployable engineering guide, helping you avoid pitfalls and work more efficiently during design, migration, and troubleshooting.